Synopsis
There are multiple ways to apply endpoint protection to a storage platform. If you are a Microsoft shop and want to extend your Defender footprint to include your QuantaStor Software Defined Storage platform, you’re in luck! Microsoft Defender for Endpoint on Linux can allow you to provide antivirus and other endpoint protection capabilities to QuantaStor.
Microsoft Defender for Endpoint is…
… a cloud-native, enterprise-grade endpoint security platform designed to prevent, detect, investigate, and respond to advanced cyber threats across multiple platforms, including Windows, macOS, Linux, Android, iOS, and IoT devices. It leverages AI, machine learning, and global threat intelligence to provide next-generation protection, endpoint detection and response (EDR), attack surface reduction, and automated investigation and remediation.
QuantaStor is…
… an enterprise-grade Software Defined Storage platform that turns standard servers into multi-protocol, scale-out storage appliances and delivers file, block, and object storage. OSNexus has made managing enterprise-grade, performant scale-out storage (Ceph-based) and scale-up storage (ZFS-based) extremely simple in QuantaStor, and able to be done quickly from anywhere. The differentiating Storage Grid technology makes storage management a breeze.
At a Glance
In this post I will discuss the implementation of Microsoft Defender for Endpoint on Linux directly on QuantaStor. We’ll go through onboarding, management through the Microsoft Defender portal and some light testing to validate that we’re not going to lose a bunch of storage performance by running endpoint processing on the storage node. It should be noted that Defender for Endpoint can also be managed through Microsoft Intune but that will not be covered here.
DISCLAIMER: I am not a Microsoft Defender expert and only offer the information I’ve discovered through the process of doing this activity. Regarding licensing, my account was allocated a Microsoft Defender for Endpoint P2 license.
Let’s Go!
Here’s the agenda:
- Discuss the licensing and account roles required to configure and manage Defender for Endpoint
- “Onboard” the QuantaStor node to the Microsoft Defender platform
- Validate installation
- Discuss security policies
- Discuss endpoint performance
Activity Components
For this article, I’m using a single QuantaStor virtual machine running on VMware vSphere:
- vCPUs: 6
- RAM: 8GB
- OS: QuantaStor 6.5
- Networking: Two 10GB connections, one for management and one for data
- Storage:
- 1 x 100GB SSD for QS OS install/boot
- 2 x 100GB SSDs for read and write cache
- 4 x 10GB SSDs for data
With that configuration I created a 4-disk zpool and then created a single NFS network share.
Microsoft Licensing and Account Roles
Microsoft licensing has always been a complex topic and I’m not going to go very deep. Microsoft Defender for Endpoint supports Linux through specific server licenses. To onboard Linux servers, it’s my understanding that you need one of the following licenses:
- Microsoft Defender for Servers Plan 1 or Plan 2
- Microsoft Defender for Endpoint for Servers
- Microsoft Defender for Business Servers (for small and medium-sized businesses only)
To be able to interact with Microsoft Defender you need to have the appropriate role(s) assigned to your Microsoft 365 account. In the Microsoft 365 Admin Center or Microsoft Entra Admin Center you need to be granted one or more of the following roles, depending on your responsibilities:
| Role | Scope | Capabilities |
|---|---|---|
| Security Administrator | Organization-wide | Can manage security policies, alerts, and settings in Microsoft 365 Defender. Can onboard devices. Cannot manage licenses. |
| Security Operator | Organization-wide | Can view alerts and reports and take response actions, but cannot change policies. |
| Global Administrator | Organization-wide | Full access to all Microsoft 365 services, including Defender for Endpoint. Typically overkill unless required. |
For my account we added both of the security roles.

“Onboarding” QuantaStor to Microsoft Defender
Now that your account has the appropriate roles applied to it, you should be able to access the Microsoft Defender portal, and that’s going to give us access to the portal resources we need to use for onboarding.
Login to the Microsoft Defender portal.
Scroll all the way down in the left pane and click on Settings.

In Settings, click Endpoints.
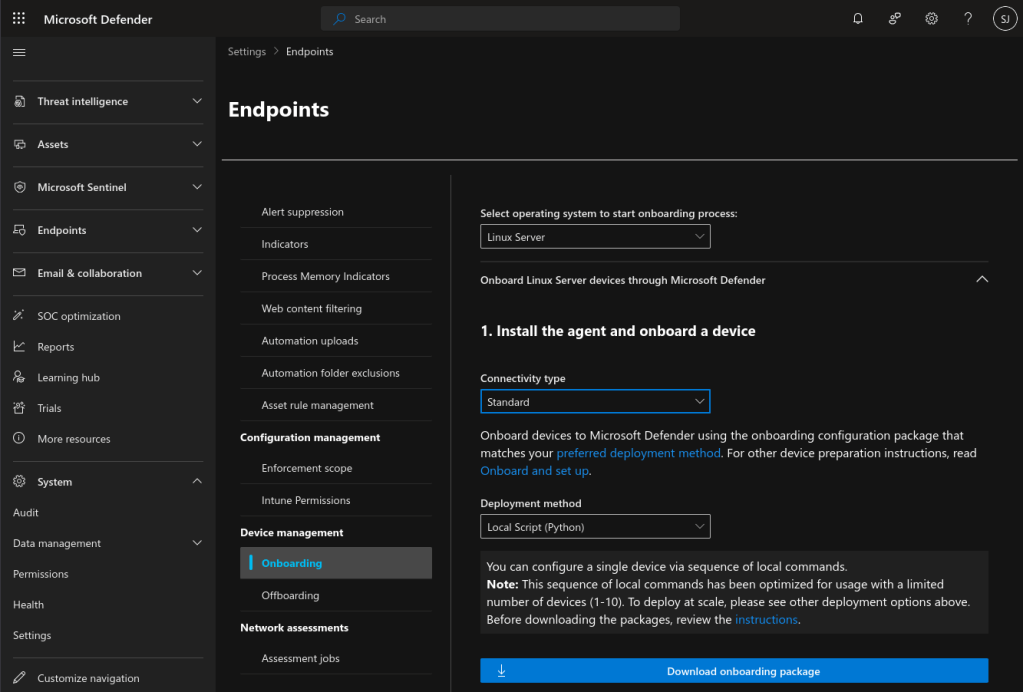
Scroll down in the Endpoints left pane and click Onboarding. Make the following selections:
- Operating System: Linux Server
- Connectivity Type: Standard
- Deployment Method: Local Script (Python)
Then click “Download onboarding package”.
Next, use SCP to copy the onboarding package to the qadmin home directory on the QuantaStor server. Then start an SSH session to the QuantaStor server to complete the installation.
# From local machine, copy onboarding package to server and start SSH session jordahl@local:~$ scp WindowsDefenderATPOnboardingPackage.zip qadmin@10.0.18.33: qadmin@10.0.18.33's password: WindowsDefenderATPOnboardingPackage.zip jordahl@local:~$ ssh qadmin@10.0.18.33 qadmin@10.0.18.33's password: Linux sj-643f-33 6.5.0-35-generic #35~22.04.1-Ubuntu SMP PREEMPT_DYNAMIC Tue May 7 09:00:52 UTC 2 x86_64 x86_64 x86_64 GNU/Linux Ubuntu 22.04.4 LTS OSNEXUS QuantaStor 6.6.0.357+next-2834f7ef78 == System Info == Uptime: up 10 minutes CPU: 6 cores RAM: 7.74625 GB System information as of Wed Oct 8 10:38:22 PM UTC 2025 System load: 0.05 Processes: 385 Usage of /: 23.0% of 56.38GB Users logged in: 0 Memory usage: 15% IPv4 address for ens192: 10.0.18.33 Swap usage: 0% Last login: Tue Oct 7 10:16:54 2025 from 10.0.41.19 # Download, unzip, chmod and run installer script qadmin@sj-643f-33:~$ wget https://raw.githubusercontent.com/microsoft/mdatp-xplat/refs/heads/master/linux/installation/mde_installer.sh --2025-10-08 22:39:07-- https://raw.githubusercontent.com/microsoft/mdatp-xplat/refs/heads/master/linux/installation/mde_installer.sh Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ... Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 63207 (62K) [text/plain] Saving to: ‘mde_installer.sh’ mde_installer.sh 100%[========================================================>] 61.73K --.-KB/s in 0.003s 2025-10-08 22:39:07 (17.5 MB/s) - ‘mde_installer.sh’ saved [63207/63207] qadmin@sj-643f-33:~$ unzip WindowsDefenderATPOnboardingPackage.zip Archive: WindowsDefenderATPOnboardingPackage.zip inflating: MicrosoftDefenderATPOnboardingLinuxServer.py qadmin@sj-643f-33:~$ chmod +x mde_installer.sh qadmin@sj-643f-33:~$ sudo ./mde_installer.sh --install --onboard ./MicrosoftDefenderATPOnboardingLinuxServer.py --channel prod --min_req [sudo] password for qadmin: [i] Specify the version to be installed using "--mdatp" argument. If not provided, latest mde will be installed by default. --- mde_installer.sh v0.8.2 --- [v] minimal requirements met [v] detected: x86_64 architecture [v] detected: ubuntu 22.04 jammy (debian) [v] scaled: 22.04 [v] set package manager: apt [v] no conflicting applications found [>] installing apt-transport-https [>] configuring the repository [>] installing MDE [v] Installation complete! [>] onboarding script: ./MicrosoftDefenderATPOnboardingLinuxServer.py [v] Onboarded [v] --- mde_installer.sh ended. --- [*] exiting (0) qadmin@sj-643f-33:~$
If you go into the Microsoft Defender portal, expand Assets and select Devices, at first you’ll see nothing… Hmmm…
Give it a little while to cook. When done you’ll then see the node you just onboarded.
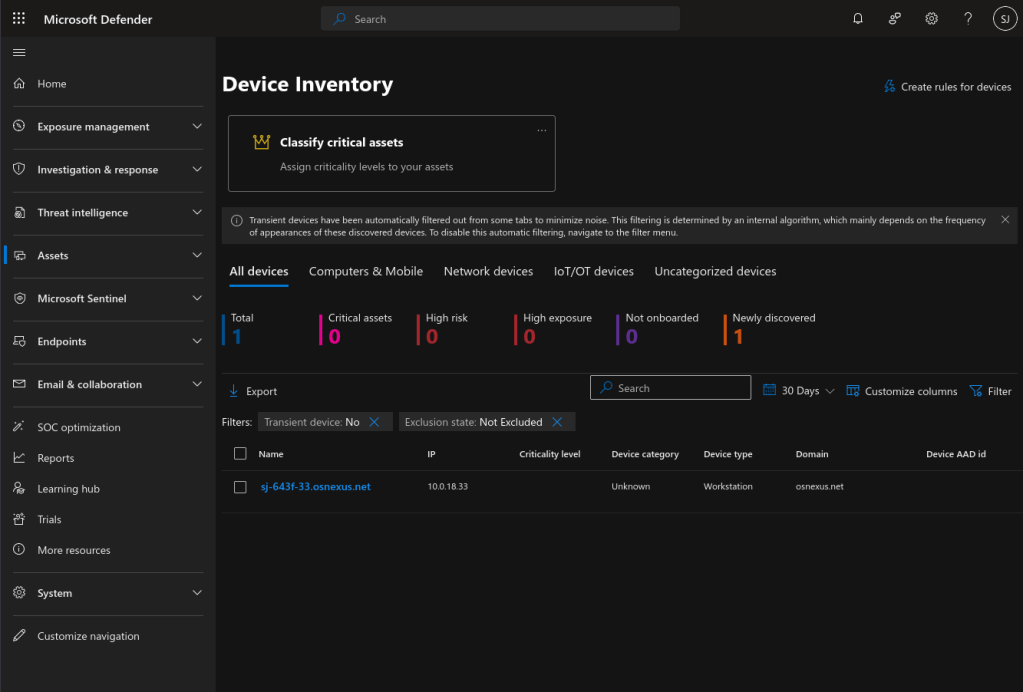
Validate Installation
Now let’s intentionally throw some viruses at the system to see how it responds.
qadmin@sj-643f-33:~$ mdatp health --field real_time_protection_enabled false qadmin@sj-643f-33:~$ sudo mdatp config real-time-protection --value enabled [sudo] password for qadmin: Configuration property updated. qadmin@sj-643f-33:~$ curl -o /tmp/eicar.com.txt https://secure.eicar.org/eicar.com.txt % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 68 100 68 0 0 94 0 --:--:-- --:--:-- --:--:-- 94 qadmin@sj-643f-33:~$ curl -o /tmp/eicar_com.zip https://secure.eicar.org/eicar_com.zip % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 184 100 184 0 0 274 0 --:--:-- --:--:-- --:--:-- 274 qadmin@sj-643f-33:~$ curl -o /tmp/eicarcom2.zip https://secure.eicar.org/eicarcom2.zip % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 308 100 308 0 0 444 0 --:--:-- --:--:-- --:--:-- 445 qadmin@sj-643f-33:~$ mdatp threat list Id: "b19719ee-85bc-4dbc-82ee-c26ec5a0fc76" Name: Virus:DOS/EICAR_Test_File Type: "virus" Detection time: Wed Oct 8 22:51:38 2025 Status: "quarantined" --- Id: "73df7817-b287-4f33-b769-4ee79b27203d" Name: Virus:DOS/EICAR_Test_File Type: "virus" Detection time: Wed Oct 8 22:53:05 2025 Status: "quarantined" --- Id: "c008cd8d-ce65-4be2-90ec-3b525e91191a" Name: Virus:DOS/EICAR_Test_File Type: "virus" Detection time: Wed Oct 8 22:53:16 2025 Status: "quarantined" qadmin@sj-643f-33:~$ curl -L -o MDE-Linux-EDR-DIY https://aka.ms/MDE-Linux-EDR-DIY % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 829 100 829 0 0 1486 0 --:--:-- --:--:-- --:--:-- 1486 qadmin@sj-643f-33:~$ unzip MDE-Linux-EDR-DIY Archive: MDE-Linux-EDR-DIY inflating: mde_linux_edr_diy.sh qadmin@sj-643f-33:~$ chmod +x mde_linux_edr_diy.sh qadmin@sj-643f-33:~$ ./mde_linux_edr_diy.sh Reading package lists... Done Building dependency tree... Done Reading state information... Done curl is already the newest version (7.81.0-1ubuntu1.21). The following NEW packages will be installed: zip 0 upgraded, 1 newly installed, 0 to remove and 91 not upgraded. Need to get 176 kB of archives. After this operation, 544 kB of additional disk space will be used. Get:1 http://archive.ubuntu.com/ubuntu jammy/main amd64 zip amd64 3.0-12build2 [176 kB] Fetched 176 kB in 1s (199 kB/s) Selecting previously unselected package zip. (Reading database ... 164512 files and directories currently installed.) Preparing to unpack .../zip_3.0-12build2_amd64.deb ... Unpacking zip (3.0-12build2) ... Setting up zip (3.0-12build2) ... Processing triggers for man-db (2.10.2-1) ... Scanning processes... Scanning linux images... Running kernel seems to be up-to-date. No services need to be restarted. No containers need to be restarted. No user sessions are running outdated binaries. No VM guests are running outdated hypervisor (qemu) binaries on this host. /tmp/support_files.wOs3rM /home/qadmin adding: tmp/support_files.wOs3rM/file_example.doc (stored 0%) adding: tmp/support_files.wOs3rM/file_example.pptx (stored 0%) adding: tmp/support_files.wOs3rM/file_example.pdf (stored 0%) adding: tmp/support_files.wOs3rM/file_example.txt (stored 0%) adding: tmp/support_files.wOs3rM/file_example.docx (stored 0%) Reading package lists... Done Reading state information... Done The following packages will be REMOVED: zip 0 upgraded, 0 newly installed, 1 to remove and 91 not upgraded. After this operation, 544 kB disk space will be freed. (Reading database ... 164525 files and directories currently installed.) Removing zip (3.0-12build2) ... Processing triggers for man-db (2.10.2-1) ... Completed Successfully qadmin@sj-643f-33:~$
You’ll notice that when we issued the mdatp threat list command that it caught the files that we downloaded. The remaing commands should have raised a detection in the Microsoft Defender portal.
Before we switch to that, one more CLI command. This will show you what the local agent believes about its health. You can determine state, versions, expirations, update timestamps and a bunch more.
qadmin@sj-643f-33:~$ mdatp health healthy : true health_issues : [] licensed : true engine_version : "1.1.25070.6000" engine_load_status : "Engine load succeeded" app_version : "101.25082.0003" org_id : "cb83e3bc-4a67-4c97-ac90-693e583a3b08" log_level : "info" machine_guid : "a7900342-31b2-d247-1597-e5bbcd490f7e" release_ring : "Production" product_expiration : Jun 04, 2026 at 01:55:31 PM cloud_enabled : true cloud_automatic_sample_submission_consent : "safe" cloud_diagnostic_enabled : false cloud_pin_certificate_thumbs : false passive_mode_enabled : false behavior_monitoring : "disabled" real_time_protection_enabled : true real_time_protection_available : true real_time_protection_subsystem : "fanotify" supplementary_events_subsystem : "ebpf" automatic_definition_update_enabled : true definitions_updated : Oct 24, 2025 at 10:44:30 PM definitions_updated_minutes_ago : 35 definitions_version : "1.439.427.0" definitions_status : "up_to_date" edr_early_preview_enabled : "disabled" edr_device_tags : [] edr_group_ids : "" edr_configuration_version : "30.199999.w7r0.2025.10.23.03-3509817d9628fcfd50ef93e71bc76ffff24ef050" edr_machine_id : "acd935b5c30f2b315066ea444712a7c063ebaf74" conflicting_applications : [] network_protection_status : "stopped" network_protection_enforcement_level : "disabled" qadmin@sj-643f-33:~$
Now let’s bounce back into to the Microsoft Defender portal. You’ll notice that “High risk” now has a value of 1.
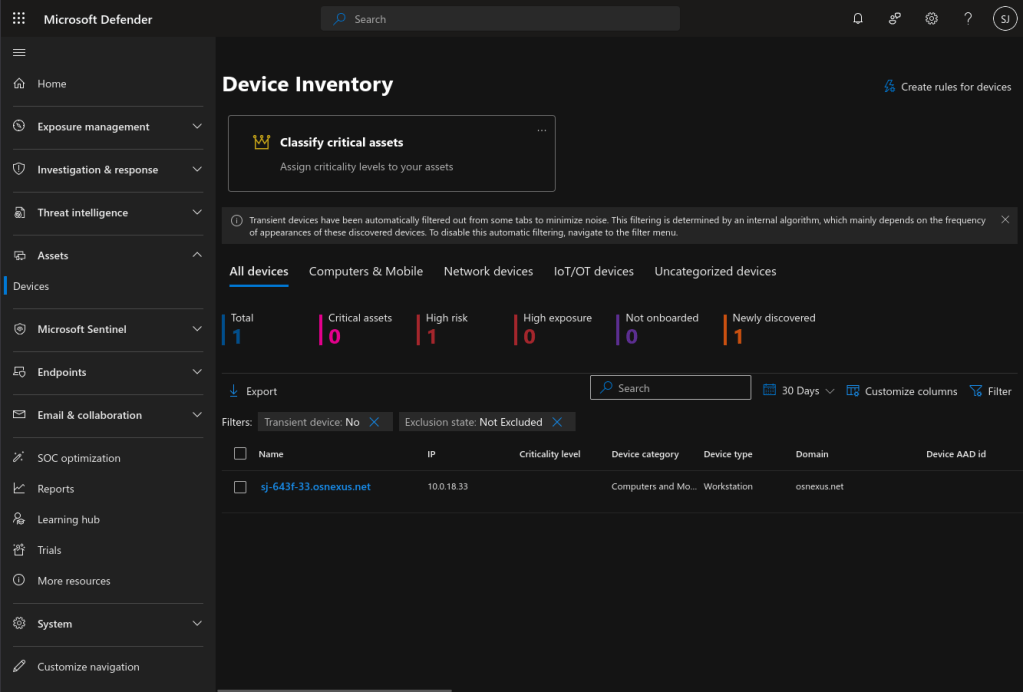
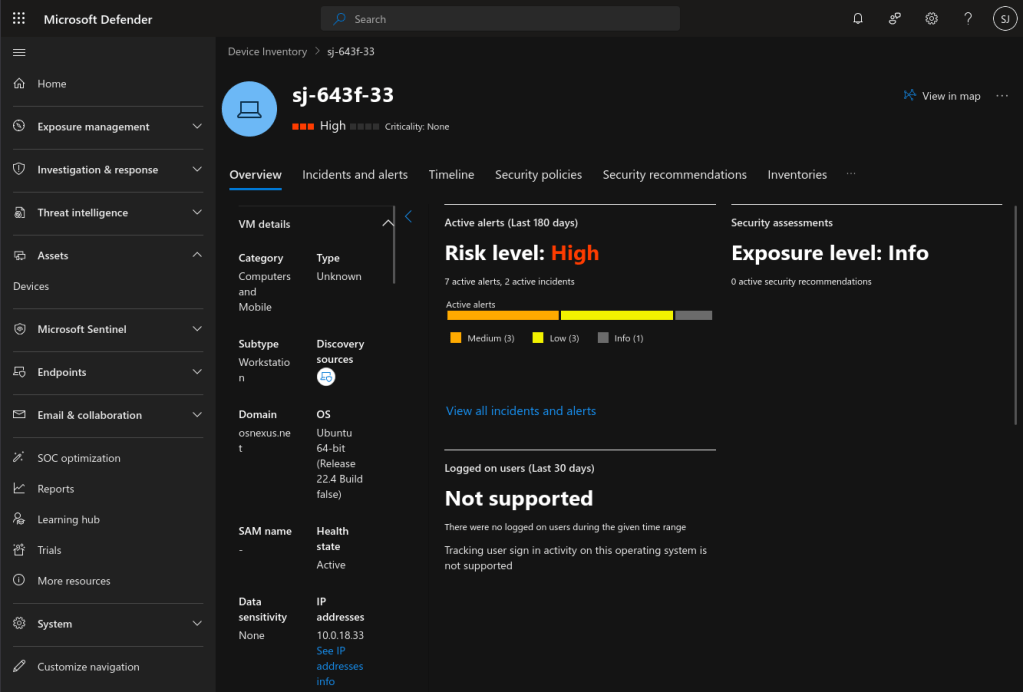
Clicking on the node allows you to get all kinds of details.
The Incidents and alerts tab/link provides a lot of detailed information about the detected threats.
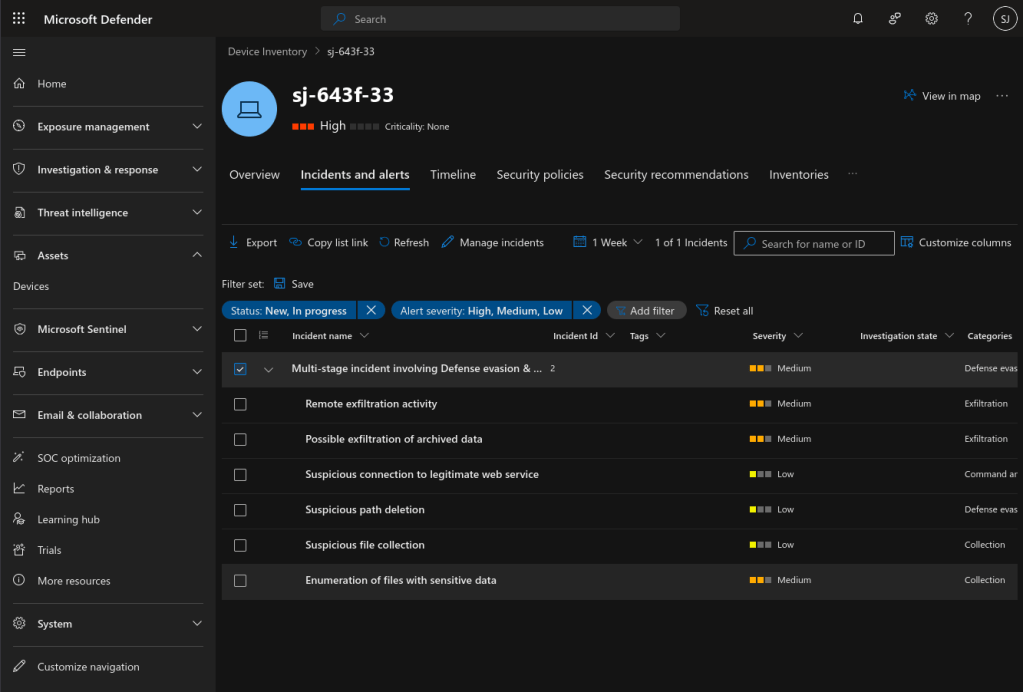
Clicking on one of the threats begins your decent into tons of deep information about the threat.
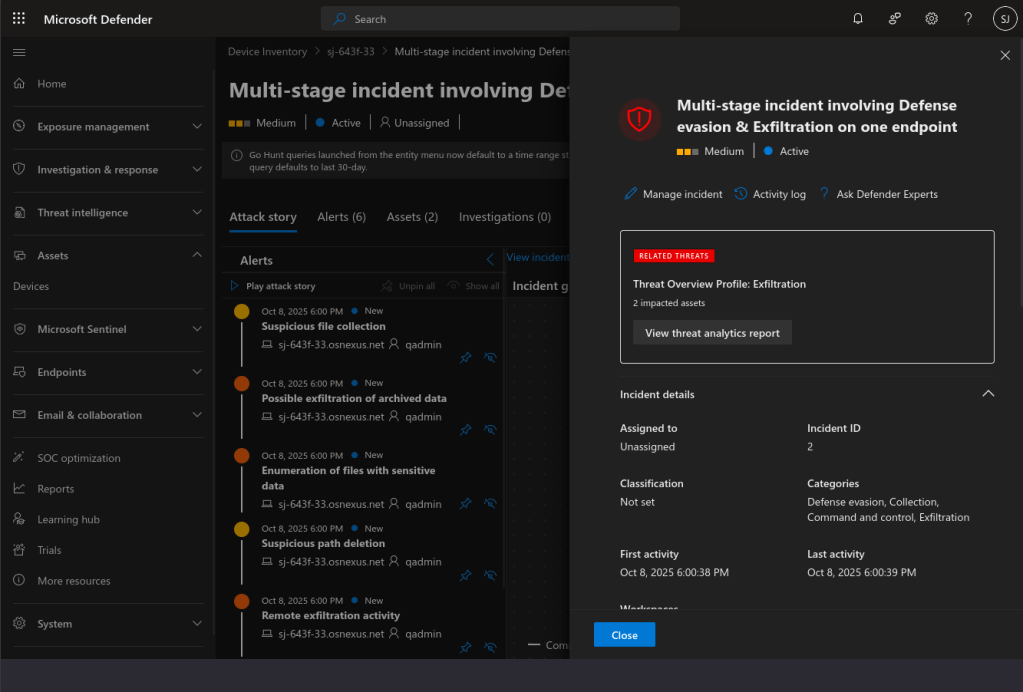
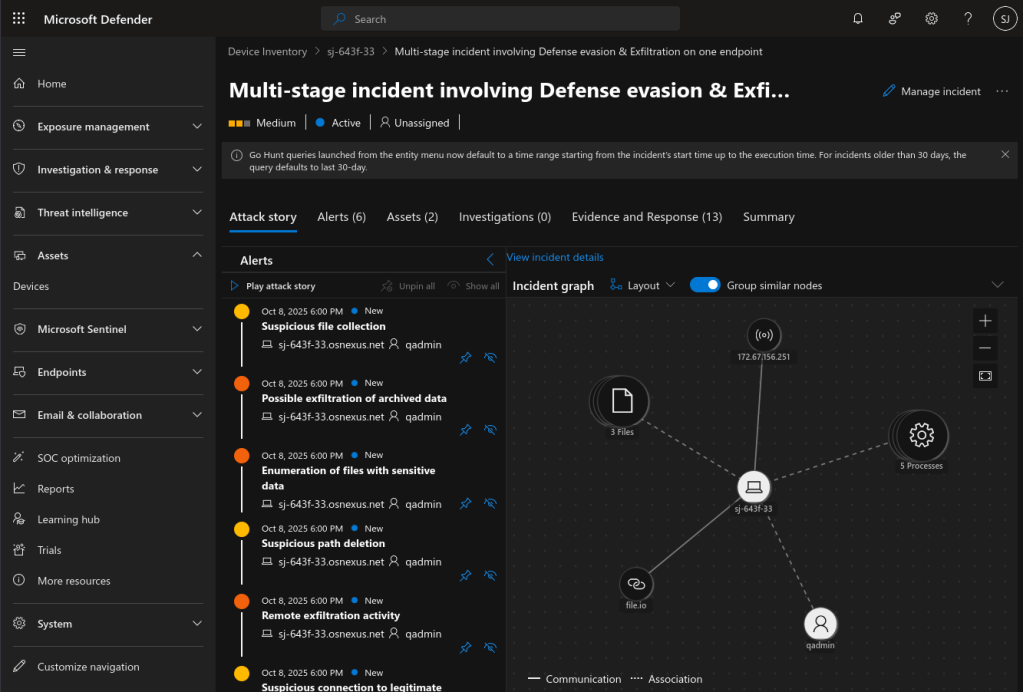
Closing the automatically opened dialog reveals a threat graph that’s part of the Attack story. The rest of the tabs give you all the data you need to determine the threat level. You can explore to your heart’s content.
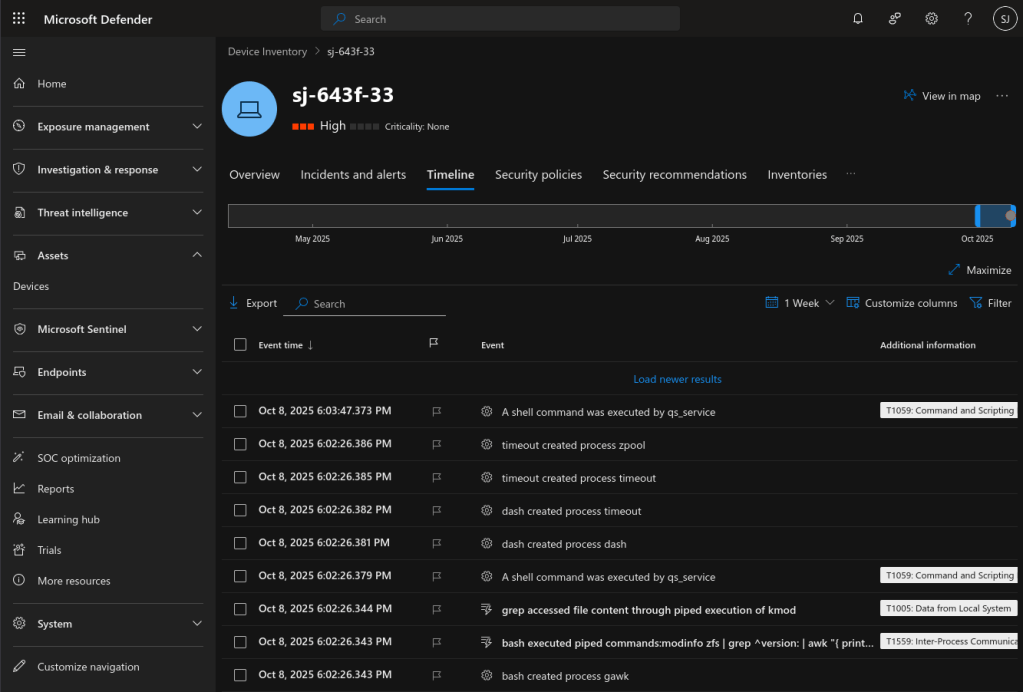
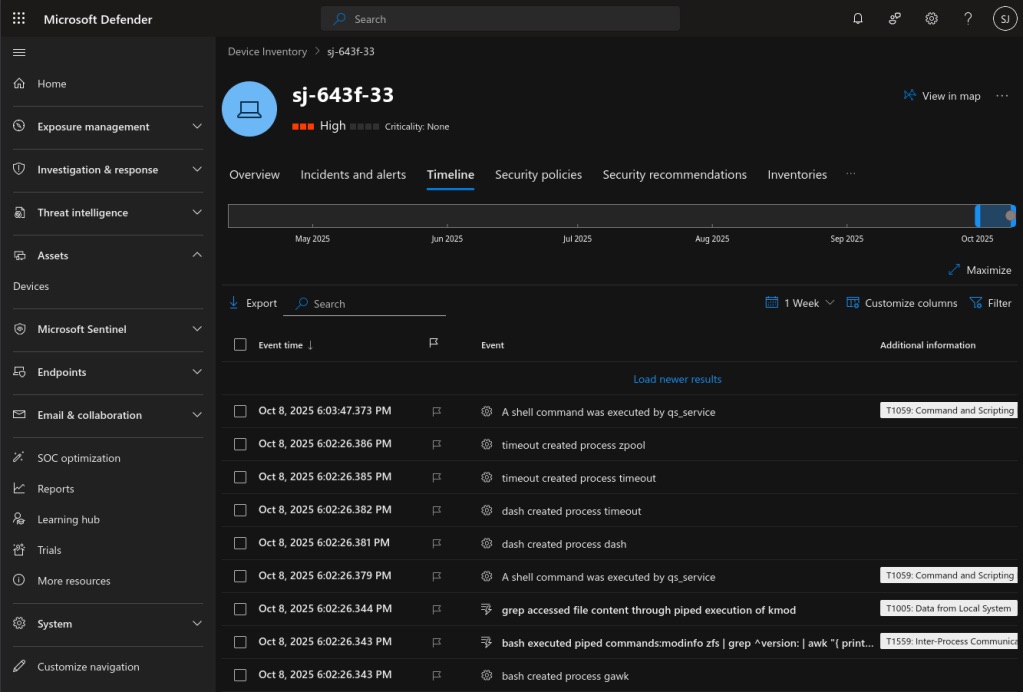
The Timeline gives you details about the series of threats that were found and you can dig into each one.
Security Policies
Defining security policies is a complex activity and is outside the scope of this article. But I didn’t want to leave you without someplace to go next. With Defender for Endpoint you have a couple options. If you want centralized management you can use the Microsoft Defender portal or Microsoft Intune. For decentralized/local management you can provide the agent on QuantaStor a JSON file that dictates what you want your security profile to be.
Here are links to the resources required to continue on:
Endpoint Performance Characteristics
Any storage administrator is going to be at least curious about the performance impact of adding endpoint protection processes on a storage array. To that end I decided to run some Iozone tests before and after adding Microsoft Defender for Endpoint to the QuantaStor node.
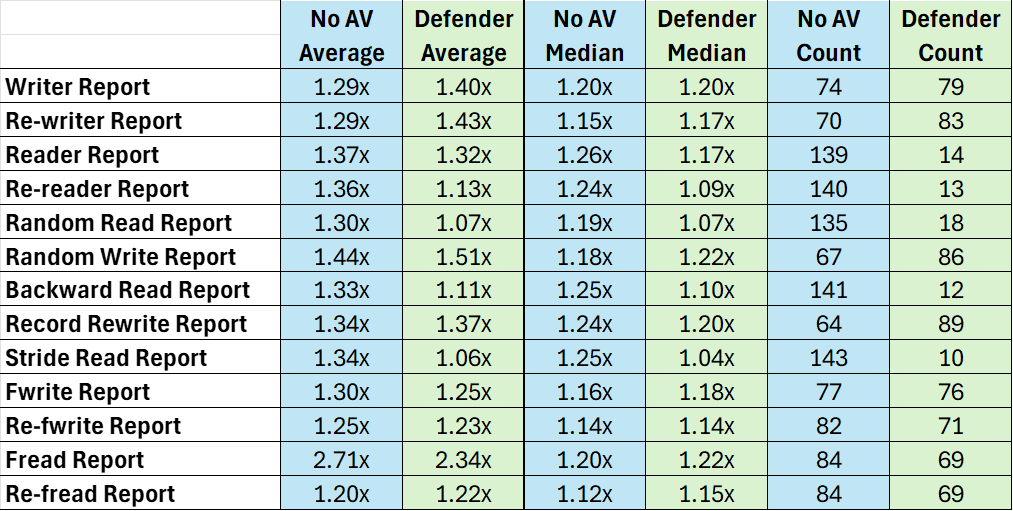
Let’s dissect this. First, “No AV …” is the test that was run before install and “Defender …” is the test that was run after. For each test (left column) there are 153 values collected. If we first look at the two columns on the right, those numbers represent the number of times a test value was greater than the corresponding value in the other test. So for the Writer Report test, 79 of the 153 test values in the Defender test were greater than the corresponding value in the No AV test, and 74 of the 153 values were greater for the No AV test. The Average and Median columns suggest HOW MUCH faster those 79/74 values were than the other test.
What this data tells me is that there IS a performance impact by running Defender on the QuantaStor node, but IMHO it’s not that much. There are always tradeoffs to any decision and in this case we’d be choosing endpoint protection over a potential bit of performance.
Summing it Up
Endpoint protection is important to a proper corporate security posture. Microsoft Defender for Endpoint running on your QuantaStor nodes can be one more step to thwarting an attack. I hope this gave you some good insight of what to expect when deploying.
I’d love to hear feedback from your adventure deploying this. Please start a comment thread and let me know how it went. Or if you want the deeper dive into my results I’d love to discuss it with you.
If you have ideas for additional posts that would be valuable to you please don’t hesitate to drop me a line and share them at steve.jordahl (at) osnexus.com!
Useful Resources
- Use installer script based deployment to deploy Microsoft Defender for Endpoint on Linux
- Prerequisites for Microsoft Defender for Endpoint on Linux
- Deploy Microsoft Defender for Endpoint on Linux manually
- Microsoft 365 Admin Center
- Microsoft Defender Portal
- Microsoft Intune
- Microsoft Entra
- mdatp Linux Install Script
- Security Policy Management via:
Leave a comment